在我的經驗中,其實 Windows Server 算是滿強悍的,無論是在效能或是安全性上。當然,主要的原因還是管理者需要夠了解底層,以及勤勞的上 hotfix。
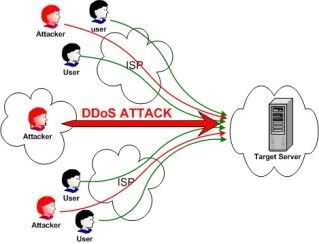
曾 經遇過 Windows Server 被 DDoS,這個問題其實很複雜,不過如果只是一般的 DDoS,包括使用 ICMP flood、syn flood、UDP flood、TCP Connection attach 等,其實 Windows 本身就可以擋掉大部分。
不過當流量,或是 source ip 多到一個程度的時候,還是得靠百萬元等級的硬體防火牆來擋了!
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\AFD\Parameters] "DynamicBacklogGrowthDelta"=dword:0000000a "MaximumDynamicBacklog"=dword:00004e20 "MinimumDynamicBacklog"=dword:00000014 "EnableICMPRedirect"=dword:00000000 "EnableDynamicBacklog"=dword:00000001 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services] "SynAttackProtect"=dword:00000001 "TcpMaxPortsExhausted"=dword:00000005 "TcpMaxHalfOpen"=dword:000001f4 "TcpMaxHalfOpenRetried"=dword:00000190 "TcpMaxConnectResponseRetransmissions"=dword:00000002 "TcpMaxDataRetransmissions"=dword:00000002 "EnablePMTUDiscovery"=dword:00000000 "KeepAliveTime"=dword:000493e0 "NoNameReleaseOnDemand"=dword:00000001 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters] "DisableIPSourceRouting"=dword:00000001 "EnableFragmentChecking"=dword:00000001 "EnableMulticastForwarding"=dword:00000000 "IPEnableRouter"=dword:00000000 "EnableDeadGWDetect"=dword:00000000 "EnableAddrMaskReply"=dword:00000000













![Win 10 升級失敗 - [你無法使用安裝程式在USB快閃磁碟機上安裝windows]](/sysdata/doc/4/49de9fb6d5b097a6/7216_m.jpg)